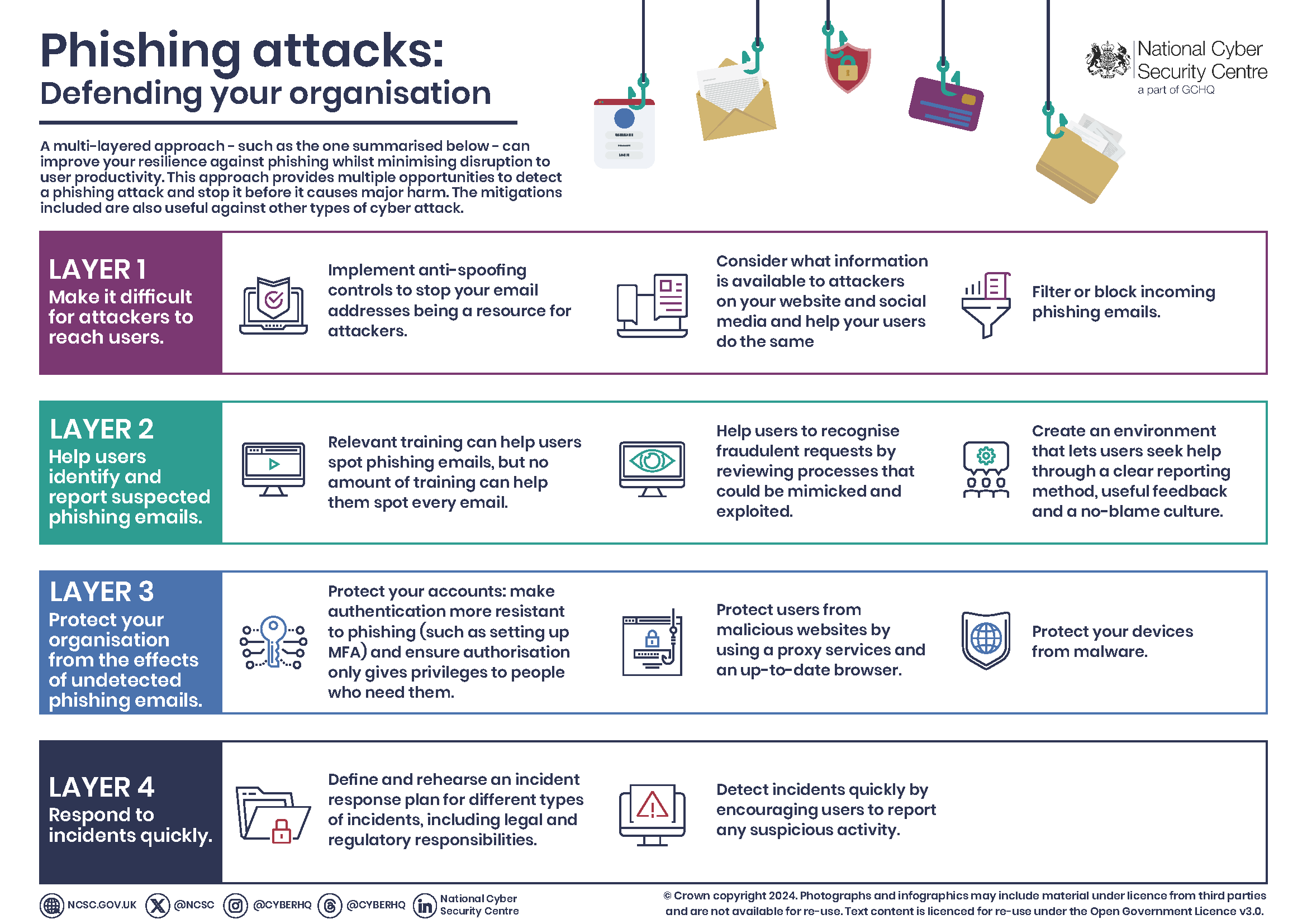
Phishing attacks are common and dangerous. They trick you into giving up personal information.
Recognizing these threats is crucial to staying safe online. Phishing attacks use fake emails, websites, and messages. They look real, so many people get fooled. These scams can steal passwords, credit card numbers, and other sensitive data. Knowing how to spot these tricks can save you from a lot of trouble.
In this guide, you will learn how to detect phishing attacks. You’ll also find out how to protect yourself and your information. Stay alert, stay informed, and keep your personal details secure. Let’s dive into the steps to keep you safe from phishing attacks.
Recognizing Phishing Emails
In today’s digital age, phishing emails have become a significant threat. These deceptive messages are designed to trick you into revealing personal information or clicking on malicious links. Recognizing phishing emails is crucial to staying safe online. Let’s dive into some telltale signs of these dangerous emails.
Suspicious Sender Addresses
One of the first things to check in an email is the sender’s address. Phishers often use email addresses that mimic legitimate ones but with slight variations. Here’s what you should look for:
- Misspelled domains: For example, instead of info@bank.com, you might see info@bnak.com.
- Unfamiliar senders: If you receive an email from a sender you don’t recognize, proceed with caution.
- Generic addresses: Emails from addresses like support@service.com instead of a specific company’s domain can be suspicious.
A quick tip: Hover over the sender’s name to see the full email address. This can reveal discrepancies that aren’t immediately obvious.
Unusual Language And Grammar
Phishing emails often contain language that seems off. This could be due to poor translation or simply because the phisher is in a hurry. Here are some red flags:
- Grammatical errors: Legitimate companies usually proofread their emails. Multiple typos or awkward phrasing can be a sign of a phishing attempt.
- Urgent language: Phrases like “Immediate action required” or “Your account will be suspended” are designed to create panic and rush you into acting without thinking.
- Unusual greetings: Generic greetings like “Dear Customer” instead of using your actual name can indicate a phishing email.
Remember, if it sounds too urgent or too good to be true, it probably is. Take a moment to assess the email’s language and grammar before clicking on any links or providing any information.
By paying attention to these details, you can better protect yourself from phishing attacks. Stay vigilant, and always think twice before interacting with suspicious emails. After all, it’s better to be safe than sorry!
Credit: www.ncsc.gov.uk
Identifying Malicious Links
Phishing attacks often rely on tricking you with malicious links. These links might seem harmless but lead to dangerous websites. Learning how to spot these links can protect you from scams and data theft.
Hover Over Links
Always hover over links before clicking. This simple action can reveal a lot. When you hover, the true URL appears at the bottom of your browser. Check this URL carefully. Does it look suspicious? Does it match the website you expect? If something feels off, do not click.
Check Url Legitimacy
Phishers often use URLs that look almost real. They might change a single letter or add extra words. This trick fools many people. Always double-check the URL for small changes. Look for misspelled words or extra characters. Legitimate sites usually have straightforward URLs. Use a search engine to find the official website if unsure.
Analyzing Attachments
When it comes to phishing attacks, one of the most common tactics cybercriminals use is sending malicious attachments. These can look innocent but can wreak havoc on your device and personal information. In this section, we’ll dive into how to analyze attachments to detect phishing attempts and keep yourself safe. Let’s break it down into two key areas: Unexpected Attachments and File Type Awareness.
Unexpected Attachments
Have you ever received an email with an attachment you weren’t expecting? It’s like getting a surprise gift from a stranger—exciting, but a bit suspicious. Always be cautious with unexpected attachments. Here’s a quick checklist to help you:
- Check the sender: Do you recognize the email address? If not, it’s a red flag.
- Look for typos: Phishing emails often have spelling mistakes or poor grammar.
- Verify with the sender: If the email claims to be from someone you know, contact them through another method to confirm they actually sent it.
Think of it like this: if you weren’t expecting a package, would you just open it without checking who it’s from? Probably not. The same caution should apply to email attachments.
File Type Awareness
Not all file types are created equal. Some are more likely to be used by cybercriminals. Here’s a simple table to help you understand which file types are safe and which ones you should be wary of:
| File Type | Risk Level |
|---|---|
| .exe | High |
| .zip | Medium |
| Medium | |
| .doc/.docx | Low to Medium |
| .jpg/.png | Low |
Executable files (.exe) are the most dangerous. They can install malware on your computer. Compressed files (.zip) and documents (.pdf, .doc) can also be risky, as they might contain hidden malware or scripts.
So, what’s the takeaway? Always think twice before downloading or opening an attachment, especially if it’s an unusual file type or from an unknown sender. Remember, it’s better to be safe than sorry.
By keeping these tips in mind, you’ll be much better equipped to spot and avoid phishing attacks. Stay vigilant, stay safe!
Spotting Fake Websites
Learn to spot fake websites to protect yourself from phishing attacks. Check website URLs carefully and look for security indicators. Always verify the site’s legitimacy before entering personal information.
Spotting fake websites can save you from phishing attacks. Cybercriminals create sites that look real. But they’re fake. Learning to spot these sites is key. Here are some tips to help you.Check For Https
The first step is to check for HTTPS. Look at the website’s URL. It should start with “https://”. The “s” stands for secure. This means the site encrypts data. If a site only has “http://”, avoid it. It’s not safe.Look For Misspellings
Fake websites often have misspellings. Look closely at the URL. Even a small typo can be a red flag. Check the website content too. Spelling errors or bad grammar are signs of a scam. Real businesses usually check their sites for errors. Be cautious if you see mistakes.Understanding Social Engineering Tactics
Understanding social engineering tactics is crucial in recognizing phishing attacks. Cybercriminals use these tactics to manipulate and deceive you. They exploit human emotions and behaviors to gain your trust. Knowing these tactics helps you stay safe online.
Urgency And Fear Tactics
Phishers often create a sense of urgency. They want you to act quickly. They may claim your account is compromised. Or say you have a limited time to respond. This pressure makes you less cautious. You might not think clearly under stress. Always take a moment to verify the message.
Impersonation Techniques
Impersonation is a common social engineering tactic. Attackers pretend to be someone you trust. They might pose as a bank, a coworker, or a friend. They often mimic the tone and style of the real person or organization. They use logos, email addresses, and language that seem legitimate. Always double-check the sender’s details. Verify their identity through another channel if needed.

Credit: www.slideteam.net
Protecting Personal Information
Phishing attacks are becoming more sophisticated, and protecting your personal information online is more crucial than ever. Hackers are constantly finding new ways to steal sensitive data, and it’s up to you to stay vigilant. But don’t worry, staying safe is easier than you think. In this section, we’ll explore practical tips to keep your personal information secure.
Avoid Sharing Sensitive Data
One of the simplest ways to protect your personal information is to avoid sharing sensitive data online. This includes your Social Security number, bank details, and passwords. Think of these pieces of information as the keys to your kingdom. Would you hand out your house keys to a stranger? Probably not. So, be just as cautious with your personal data online.
Here are some tips to help you avoid sharing sensitive data:
- Never share your passwords or PINs, not even with friends or family.
- Avoid clicking on links in unsolicited emails or messages; they could be phishing attempts.
- Be wary of websites that ask for more information than necessary. If a site asks for your mother’s maiden name just to sign up for a newsletter, it’s a red flag.
Use Two-factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your online accounts. It’s like having a second lock on your door. Even if someone steals your password, they won’t be able to access your account without the second factor. It’s a simple yet powerful way to protect your personal information.
Here’s how 2FA works:
- You log in with your username and password.
- You’re prompted to enter a code sent to your phone or email.
- You enter the code, and voilà, you’re in.
Many online services, like email providers and social media platforms, offer 2FA. Enable it wherever possible to add an extra shield of protection.
In conclusion, protecting personal information is all about being cautious and using the tools available to you. By avoiding sharing sensitive data and using two-factor authentication, you can significantly reduce the risk of falling victim to phishing attacks. Remember, it’s better to be safe than sorry!
Using Security Tools
In today’s digital age, phishing attacks have become increasingly sophisticated. However, using the right security tools can help you stay one step ahead of cybercriminals. These tools can act as your first line of defense, making it harder for hackers to access your personal information. Let’s dive into some essential security tools you should consider.
Install Anti-phishing Software
Anti-phishing software is like having a vigilant security guard for your computer. It actively scans for suspicious activities and alerts you before any harm is done. Here’s how you can benefit from installing anti-phishing software:
- Real-time Protection: This software monitors your online activities and stops phishing attempts instantly.
- Automatic Blocking: It blocks access to malicious websites, reducing the risk of falling victim to scams.
- User-Friendly Interface: Most anti-phishing tools are designed to be easy to use, even for non-tech-savvy individuals.
Imagine you’re browsing the internet and you accidentally click on a suspicious link. Without anti-phishing software, you might not even realize you’re being scammed until it’s too late. But with the software installed, you’ll get an immediate alert, saving you from potential trouble. Think of it as your personal cyber bodyguard!
Regularly Update Security Programs
Updating your security programs might sound like a hassle, but it’s crucial. Cyber threats are always evolving, and keeping your software up to date ensures you have the latest protection. Here’s why you should make it a priority:
- Enhanced Security: Updates often include patches for newly discovered vulnerabilities.
- Improved Performance: Regular updates can also enhance the overall performance of your security tools.
- New Features: Sometimes, updates come with new features that provide better protection.
Remember that time when you ignored your software’s update notification, only to find out later that a new feature could have saved you a lot of trouble? Don’t let that happen again. Set reminders or enable automatic updates to ensure your programs are always up to date. It’s a small effort for a huge peace of mind!
By using these security tools, you can significantly reduce the risk of falling victim to phishing attacks. Stay vigilant, keep your software updated, and you’ll be well on your way to safer online experiences.
.png?width=720&height=493&name=Key%20Signs%20of%20Phishing%20(2).png)
Credit: www.proserveit.com
Reporting Phishing Attempts
Phishing attacks are more common than you might think, and knowing how to report them can make a world of difference. Imagine opening an email that looks like it’s from your bank, but something seems off. Instead of ignoring that gut feeling, you need to take action. Reporting phishing attempts is crucial for not only protecting yourself but also helping others stay safe. Here’s how you can do it.
Notify Your It Department
Your IT department is like your personal cybersecurity team. They have the knowledge and tools to handle phishing attempts effectively. If you receive a suspicious email, forward it to your IT department immediately. They can investigate the email and take necessary actions to secure the system. Don’t forget, they are there to help you.
- Forward suspicious emails
- Provide details of the incident
- Follow their instructions
For instance, if your IT team discovers that the email contains malware, they can quarantine it and prevent it from spreading. So, never hesitate to reach out to them.
Report To Authorities
Reporting phishing attempts to authorities is another critical step. Various organizations and government bodies track phishing scams and work to shut them down. By reporting, you help create a safer online environment for everyone.
- Contact your local cybercrime unit
- Report to organizations like Anti-Phishing Working Group (APWG)
- Use online reporting tools provided by your email provider
Consider this: if everyone reported phishing attempts, the bad actors behind these scams would have a much harder time succeeding. It’s like being part of a neighborhood watch program, but for the internet.
| Steps | Details |
|---|---|
| Notify IT Department | Forward the suspicious email and provide incident details |
| Report to Authorities | Contact local cybercrime units and report to organizations like APWG |
In conclusion, taking the time to report phishing attempts is more than just a good practice; it’s a responsibility. By alerting your IT department and reporting to authorities, you contribute to a safer digital world. So, the next time you receive a suspicious email, don’t just delete it—report it!
Frequently Asked Questions
How Can You Stay Safe From Phishing?
To stay safe from phishing, avoid clicking suspicious links, verify email senders, use strong passwords, enable two-factor authentication, and keep software updated.
How Are Phishing Attacks Detected?
Phishing attacks are detected using email filters, antivirus software, and user training. Suspicious links and attachments are flagged.
What Is The Best Way To Protect Against Phishing Attacks?
The best way to protect against phishing attacks is to verify email sources, avoid clicking on suspicious links, and use security software.
What Is A Common Indicator Of A Phishing Attack?
A common indicator of a phishing attack is an unexpected email requesting personal information or containing suspicious links.
Conclusion
Staying safe from phishing attacks requires vigilance and knowledge. Always verify the sender’s details before clicking links. Use strong, unique passwords for each account. Keep your software up to date. Educate yourself on common phishing tactics. Report any suspicious emails to your provider.
By following these steps, you can protect your personal information. Stay alert, stay safe.

