Hackers track online activity through various methods. They can use malware, phishing, or social engineering tactics to access data.
In today’s digital age, our online presence has become a significant part of our lives. From social media interactions to online shopping, we leave a digital trail everywhere. But this convenience comes with risks. Hackers are constantly finding new ways to track our online activity, posing threats to our privacy and security.
Understanding how these cyber criminals operate can help us protect our personal information. In this blog, we will explore the techniques hackers use to monitor online activities. You will learn how they infiltrate systems and what measures can be taken to safeguard your digital footprint. Stay informed and stay safe online.
Introduction To Online Tracking
In today’s digital age, online tracking has become a common practice. Hackers and various entities can easily monitor your online activity. Understanding how online tracking works is crucial for safeguarding your privacy. This section will introduce you to the basics of online tracking.
What Is Online Tracking?
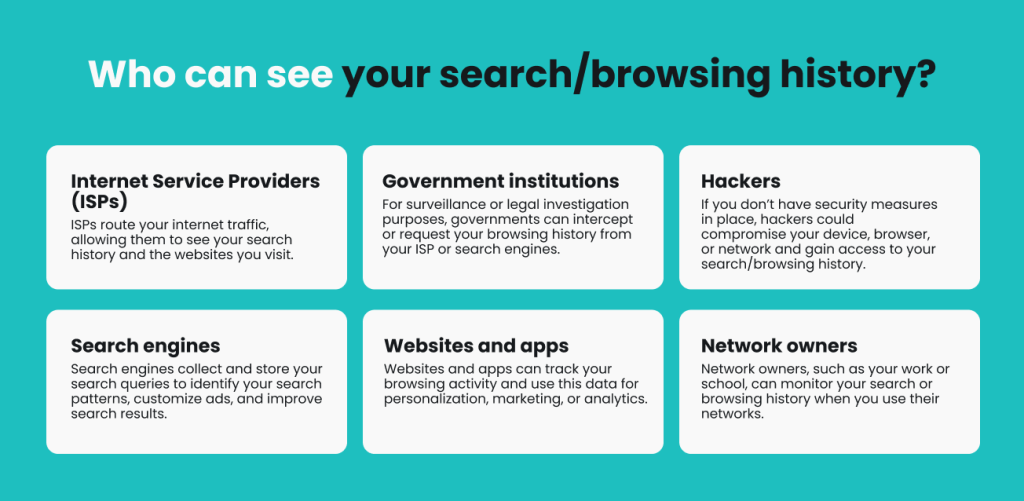
Online tracking refers to the methods used to monitor users’ online behavior. It involves collecting data about your browsing habits. This data can include the websites you visit, the links you click, and the time you spend on each page.
Hackers use various tools to track this information. They can use cookies, spyware, and other tracking technologies. These tools help them gather insights into your online activities.
Importance Of Understanding Online Tracking
Understanding online tracking is vital for protecting your personal information. When you know how tracking works, you can take steps to prevent it. This knowledge helps you stay safe from potential cyber threats.
Being aware of online tracking also enables you to make informed decisions. You can choose to use privacy-focused browsers and tools. This helps in minimizing the risk of your data being compromised.
Common Methods Of Tracking
Hackers use various methods to track online activity. Understanding these methods helps you stay safe. Here are some common ways hackers track you online.
Ip Address Tracking
Every device connected to the internet has an IP address. This is like a digital home address. Hackers can use your IP address to see your location. They can also track your online movements. Changing your IP address can make tracking harder for them.
Cookie Tracking
Websites use cookies to remember your actions. Hackers can exploit these cookies. They can see what websites you visit and what you do there. Clearing cookies regularly can reduce this risk. Be cautious with unknown websites as they might plant tracking cookies.
Advanced Tracking Techniques
When it comes to keeping tabs on your online activity, hackers have a few sophisticated tricks up their sleeves. These advanced tracking techniques can be surprisingly effective, allowing cybercriminals to gather information about you without raising any red flags. But how exactly do they do it? In this section, we’ll dive into two of the most common methods: browser fingerprinting and device fingerprinting.
Browser Fingerprinting
Let’s start with browser fingerprinting. Imagine you walk into a room full of people wearing identical masks. You’d think it’s impossible to tell them apart, right? Well, browser fingerprinting is a bit like taking off those masks. It involves collecting unique details about your web browser and using them to identify you, even if you think you’re anonymous.
How does it work? Hackers gather data points like:
- Your browser type and version
- Installed plugins
- Screen resolution
- Time zone
- Fonts you have installed
By combining these details, they create a “fingerprint” that is unique to your browser. It’s like having a digital name tag that you didn’t even know you were wearing. This fingerprint can be used to track your movements across different websites, giving hackers a clear picture of your online behavior.
Device Fingerprinting
Next up is device fingerprinting. If browser fingerprinting is taking off the masks, device fingerprinting is like reading the labels on people’s clothes. It’s a more detailed way of identifying not just the browser but the actual device you’re using.
Hackers collect information such as:
- Operating system
- Device model
- CPU type
- Battery status
- Audio settings
All these details combined make up a profile that can single out your device in a crowd. Even if you switch browsers or use private browsing modes, your device fingerprint stays the same, making it easier for hackers to track your activity over time.
It’s a bit like having a unique scent that only your device gives off. No matter where you go, it’s hard to mask completely.
So, how can you protect yourself? It’s not easy, but being aware of these techniques is the first step. Consider using tools like anti-tracking browser extensions and being mindful of the information your device shares online.
Remember, staying one step ahead of hackers requires vigilance and a bit of tech-savvy. But with the right knowledge, you can keep your online activities safe from prying eyes.

Credit: eavi.eu
Exploiting Social Media
Social media is a treasure trove for hackers. They exploit it to track online activity. Many users share too much personal information. This makes them easy targets. Let’s see how hackers use social media to their advantage.
Data Mining On Social Platforms
Hackers collect data from social media profiles. They look for personal details. This includes names, birthdays, locations, and more. They use this data to create detailed profiles. These profiles help them in future attacks.
Public posts and photos reveal a lot. Even small details can be useful. Hackers can learn about your habits and preferences. They can also see your connections and relationships. This information is valuable for their schemes.
Social Engineering Tactics
Hackers use social engineering to trick people. They pose as friends or trusted contacts. They send fake messages or emails. These messages often contain malicious links. Clicking on these links can lead to trouble.
Sometimes, hackers create fake profiles. They pretend to be someone you know. They gain your trust and gather more information. This makes their attacks more effective.
Hackers also use phishing attacks. They mimic real websites or services. They trick you into giving up your login details. With this information, they can access your accounts.
Monitoring Network Traffic
Monitoring network traffic is a common way hackers track online activity. They can see data as it moves across networks. This lets them intercept sensitive information. By understanding how this works, you can better protect your data.
Packet Sniffing
Packet sniffing is a technique hackers use to monitor network traffic. They capture and analyze data packets. These packets contain information like emails, web requests, and other data. Hackers use special tools to collect these packets. They can then read the contents and find valuable information.
Packet sniffing can be done on wired and wireless networks. On public Wi-Fi, hackers can easily sniff packets. This makes open networks risky. Always use secure connections to protect your data.
Deep Packet Inspection
Deep Packet Inspection (DPI) is a more advanced method. It involves examining the data within packets, not just the headers. DPI can identify the types of data being sent. This includes emails, web traffic, and even specific files.
Hackers use DPI to find patterns and extract useful data. They can see what websites you visit and the content you view. DPI can also bypass encryption. This makes it a powerful tool for tracking online activities.
Understanding these techniques helps you safeguard your online presence. Use VPNs and encryption to protect against packet sniffing and DPI.
Using Malware For Tracking
Cybersecurity is a critical concern in today’s digital age. One of the primary methods hackers use to track online activity is through malware. This sneaky software can infiltrate your devices without you even knowing it. But how exactly do hackers use malware to monitor your every move? Let’s delve into two of the most common types of malware used for tracking: Keyloggers and Spyware.
Keyloggers
Imagine every keystroke you make on your keyboard being recorded and sent to a hacker. That’s precisely what keyloggers do. They are a type of malware designed to capture every key you press, which can include sensitive information like passwords, credit card numbers, and private messages.
Keyloggers can be installed in several ways:
- Email Attachments: Hackers often send emails with malicious attachments. Once opened, the keylogger installs itself on your device.
- Malicious Downloads: Downloading software or files from untrustworthy sources can also lead to keylogger installation.
- Physical Access: Sometimes, the attacker has physical access to the device and installs the keylogger directly.
This malware operates in the background, often undetected, making it a potent tool for cybercriminals.
Spyware
Spyware is another form of malware that can monitor your activities. Unlike keyloggers, spyware can track a broader range of actions, including:
- Browsing history
- Emails and messages
- Application usage
Spyware can be introduced to your system in similar ways to keyloggers, such as:
- Infected websites
- Software bundles
- Phishing schemes
Once installed, spyware can relay your personal information back to the hacker, often without any visible signs. This can lead to identity theft, financial loss, and privacy breaches.
Understanding how these types of malware work is crucial to protecting yourself online. By being cautious about what you download and staying informed about the latest cybersecurity threats, you can minimize the risk of falling victim to these invasive tools.
Remember, in the world of cybersecurity, knowledge is power. Stay vigilant, stay safe!
Tracking Via Public Wi-fi
In today’s digital age, staying connected is a must. But have you ever wondered how safe it is to use public Wi-Fi? Let’s dive into how hackers track your online activity through public Wi-Fi and what you can do to protect yourself.
Risks Of Using Public Wi-fi
Public Wi-Fi networks can be a convenient way to access the internet on the go, but they come with significant risks. These networks are often unsecured, making it easy for hackers to intercept your data. Imagine sipping your coffee at your favorite café while a hacker sitting nearby is tracking your every move online. Scary, right?
Here are some key risks associated with using public Wi-Fi:
- Unsecured networks: Many public Wi-Fi networks do not use encryption, making it easy for hackers to access your data.
- Data interception: Hackers can intercept data sent over public Wi-Fi networks, including sensitive information like passwords and credit card numbers.
- Fake hotspots: Hackers can set up fake Wi-Fi hotspots to trick you into connecting, allowing them to steal your information.
Man-in-the-middle Attacks
One of the most common threats on public Wi-Fi is the man-in-the-middle (MITM) attack. This is where a hacker secretly intercepts and relays messages between two parties who believe they are directly communicating with each other.
Think of it like passing notes in class. You think you’re handing your note directly to your friend, but the person in the middle reads it and sometimes changes the content before passing it on. Here’s how it typically works:
- Connection interception: The hacker positions themselves between you and the Wi-Fi network.
- Data capture: They capture all the data you send and receive, including login credentials and personal information.
- Data manipulation: They can even alter the data, leading to misinformation or unauthorized access to your accounts.
Preventing MITM attacks requires caution. Always use secured websites (look for “HTTPS” in the URL), avoid accessing sensitive information on public Wi-Fi, and consider using a VPN (Virtual Private Network) for added security.
So next time you’re tempted to connect to that free Wi-Fi, think twice. Remember, convenience comes with its own set of risks. Stay safe and surf smart!
Credit: surfshark.com
Protecting Yourself From Tracking
Hackers often track online activity through malicious software and phishing attacks. They exploit vulnerabilities in networks and devices. Protect yourself by using strong passwords and reliable security software.
Hackers use various methods to track online activity. They often exploit vulnerabilities in networks and devices. Protecting yourself from tracking is essential for maintaining privacy and security. Here are some effective ways to safeguard your online presence.Using Vpns
A Virtual Private Network (VPN) hides your IP address. It encrypts your internet traffic. This makes it difficult for hackers to track your online activity. VPNs create a secure tunnel between your device and the internet. Always choose a reputable VPN service. Look for strong encryption and no-logs policies.Employing Anti-tracking Tools
Anti-tracking tools block tracking scripts and cookies. These scripts and cookies collect data about your online behavior. Popular browsers offer built-in anti-tracking features. You can also install browser extensions. These tools prevent websites from gathering your personal information. Regularly update your anti-tracking tools. This ensures they stay effective against new threats. “`
Credit: blog.360totalsecurity.com
Frequently Asked Questions
How Does A Hacker Track You?
A hacker tracks you using phishing, malware, social engineering, and unsecured networks. They exploit your online activities and weak passwords.
Can Someone Track My Online Activity?
Yes, your online activity can be tracked. Use VPNs, private browsing, and strong passwords to enhance privacy.
How Do I Stop People From Seeing My Browsing History?
Use incognito mode, clear your browsing history regularly, and consider using a VPN or privacy-focused browser.
How Do You Know If A Hacker Is Watching You?
Unusual device behavior, unknown apps, excessive data usage, and unexpected pop-ups may indicate a hacker is watching you.
Conclusion
Understanding how hackers track online activity is crucial for your online safety. Take steps to protect your data. Use strong passwords. Enable two-factor authentication. Stay updated with the latest security measures. Avoid suspicious links. Be cautious about sharing personal information.
Regularly monitor your accounts for unusual activity. Stay informed and proactive. Your safety online depends on your awareness. Protect yourself and your data with these simple steps. Stay safe and secure while browsing.
