Hackers use various tactics to steal personal data. Understanding these methods is key to protecting yourself.
In today’s digital age, our personal data is more vulnerable than ever. Hackers employ sophisticated techniques to gain unauthorized access to sensitive information. This can include phishing, malware attacks, and exploiting weak passwords. The consequences of data theft can be severe, leading to financial loss and identity theft.
Awareness and proactive measures can significantly reduce the risk. By recognizing the common tactics hackers use, you can better safeguard your personal information. This blog will explore the methods hackers use to steal data and provide practical tips to prevent it. Stay informed and take steps to protect your digital life.

Credit: www.esecurityplanet.com
Common Hacking Techniques
Understanding how hackers steal personal data is crucial in today’s digital age. Cybercriminals use various techniques to gain unauthorized access to sensitive information. Knowing these methods helps you protect yourself online. Let’s explore some common hacking techniques.
Phishing attacks trick users into giving away their personal information. Hackers send fake emails that look legitimate. These emails often contain links to fake websites. Users enter their details, thinking it’s a trusted site. Always check the sender’s email address. Never click on links from unknown sources.
Malware is harmful software that can damage or disable computers. Hackers use malware to steal data or spy on users. It can enter your system through email attachments or malicious websites. Install reputable antivirus software. Regularly update your system to protect against malware.
Social engineering exploits human psychology to gain information. Hackers manipulate people into giving away confidential data. They may pose as trusted individuals or create emergency situations. Be cautious of unexpected requests for personal information. Verify the identity of the person asking for sensitive data.
In man-in-the-middle attacks, hackers intercept communication between two parties. They can steal data or alter the communication. This usually happens on unsecured networks. Use secure, encrypted connections. Avoid sharing sensitive information on public Wi-Fi.

Credit: www.f-secure.com
Phishing Attacks
Phishing attacks are a common way hackers steal personal data. They trick you into giving away information. Hackers often pretend to be someone you trust. They might send you an email, text message, or even call you. This type of attack is sneaky and can happen to anyone. But don’t worry! There are ways to protect yourself. Let’s look at some types of phishing attacks and how to avoid them.
Email Phishing
Email phishing is the most common type. Hackers send emails that look real. They might pretend to be your bank or a popular website. The email will ask you to click a link or download an attachment. These links or files can steal your personal data.
- How to avoid: Never click on links or download attachments from unknown emails. Always check the sender’s email address carefully. If it looks strange, it probably is.
Spear Phishing
Spear phishing is more targeted. Hackers research their victims. They might know your name, job, or other personal details. This makes their emails look even more real. They might pretend to be a coworker or friend.
- How to avoid: Be cautious with emails that ask for personal information. Verify the sender by contacting them through another method, like a phone call.
Smishing
Smishing is phishing via SMS (text messages). Hackers send you texts that look like they are from a trusted source. The text will often have a link or a phone number to call.
- How to avoid: Do not click on links in text messages from unknown numbers. If a message looks suspicious, delete it. Always verify with the source directly.
Vishing
Vishing is phishing over the phone. Hackers call you and pretend to be from a trusted organization. They might ask for personal information or tell you to visit a website.
- How to avoid: Be cautious with phone calls asking for personal information. Hang up and call the organization directly using a number you trust.
Phishing attacks are dangerous but avoidable. By being aware and careful, you can protect your personal data. Always think twice before sharing your information. Stay safe and stay smart!
Malware Infections
Malware infections pose a significant threat to personal data. Hackers use various forms of malware to gain unauthorized access to sensitive information. Understanding these malware types can help prevent data breaches and protect your personal data.
Viruses
Viruses are harmful software programs that replicate themselves. They attach to legitimate files and programs. Once activated, they can corrupt or delete data. They can also spread to other systems through networks or removable media. Using antivirus software can help detect and remove viruses before they cause damage.
Trojans
Trojans disguise themselves as harmless software. They trick users into installing them. After installation, they create backdoors for hackers. These backdoors allow unauthorized access to your system. Avoid downloading software from untrusted sources to prevent Trojan infections.
Spyware
Spyware secretly monitors your activities. It collects sensitive information like passwords, credit card details, and browsing habits. Spyware often comes bundled with free software downloads. Using anti-spyware tools can help detect and remove these threats.
Ransomware
Ransomware encrypts your files and demands a ransom for decryption. It can spread through phishing emails or malicious websites. Paying the ransom does not guarantee file recovery. Regularly backing up your data can mitigate the effects of a ransomware attack. Stay vigilant and avoid clicking on suspicious links.
Social Engineering
Social engineering is a common tactic used by hackers to steal personal data. It involves manipulating people into giving up confidential information. Hackers use various methods to exploit human psychology. Understanding these methods can help you protect yourself from such attacks.
Impersonation
Impersonation is a technique where hackers pretend to be someone you trust. They may pose as a friend, family member, or authority figure. The goal is to gain your trust and trick you into revealing sensitive information. Always verify the identity of anyone asking for your personal data.
Pretexting
In pretexting, hackers create a false scenario to steal your data. They may call you pretending to be from your bank. They ask for your account details to resolve an issue. Always contact the institution directly to verify such requests. Do not share personal information based on unsolicited calls or messages.
Baiting
Baiting involves enticing victims with something they want. Hackers may offer free downloads or gift cards. Once you take the bait, they infect your system with malware. Avoid downloading files or clicking on links from unknown sources. Always use trusted websites and services.
Tailgating
Tailgating is a physical form of social engineering. A hacker follows someone into a secure area without permission. They exploit the trust and politeness of people. Always be cautious of letting strangers follow you into secure locations. Report any suspicious activity to security personnel.
Man-in-the-middle Attacks
Man-in-the-Middle (MitM) attacks are a common way hackers steal personal data. They intercept communication between two parties. The attacker can access and manipulate the data. These attacks occur in various forms. Understanding them helps in protecting your information.
Wi-fi Eavesdropping
Wi-Fi eavesdropping happens when hackers listen to data on public Wi-Fi networks. They can see everything you do online. This includes passwords and other sensitive information. Avoid using public Wi-Fi for banking or shopping. Use a VPN to secure your connection.
Session Hijacking
In session hijacking, hackers steal your session ID. They use it to access your online accounts. This can happen if you do not log out properly. Always log out from websites after use. Clear your cookies regularly. Enable two-factor authentication for added security.
Ssl Stripping
SSL stripping downgrades your secure HTTPS connection to an unsecure HTTP. Hackers can then read your data. Always check for HTTPS in the URL. Do not trust websites without it. Use browser extensions that enforce HTTPS for all websites.
Dns Spoofing
DNS spoofing redirects you to malicious websites. You think you are visiting a safe site, but hackers control it. This attack can lead to data theft. Use trusted DNS servers. Install anti-virus software that can detect and block malicious sites.
Protecting Personal Data
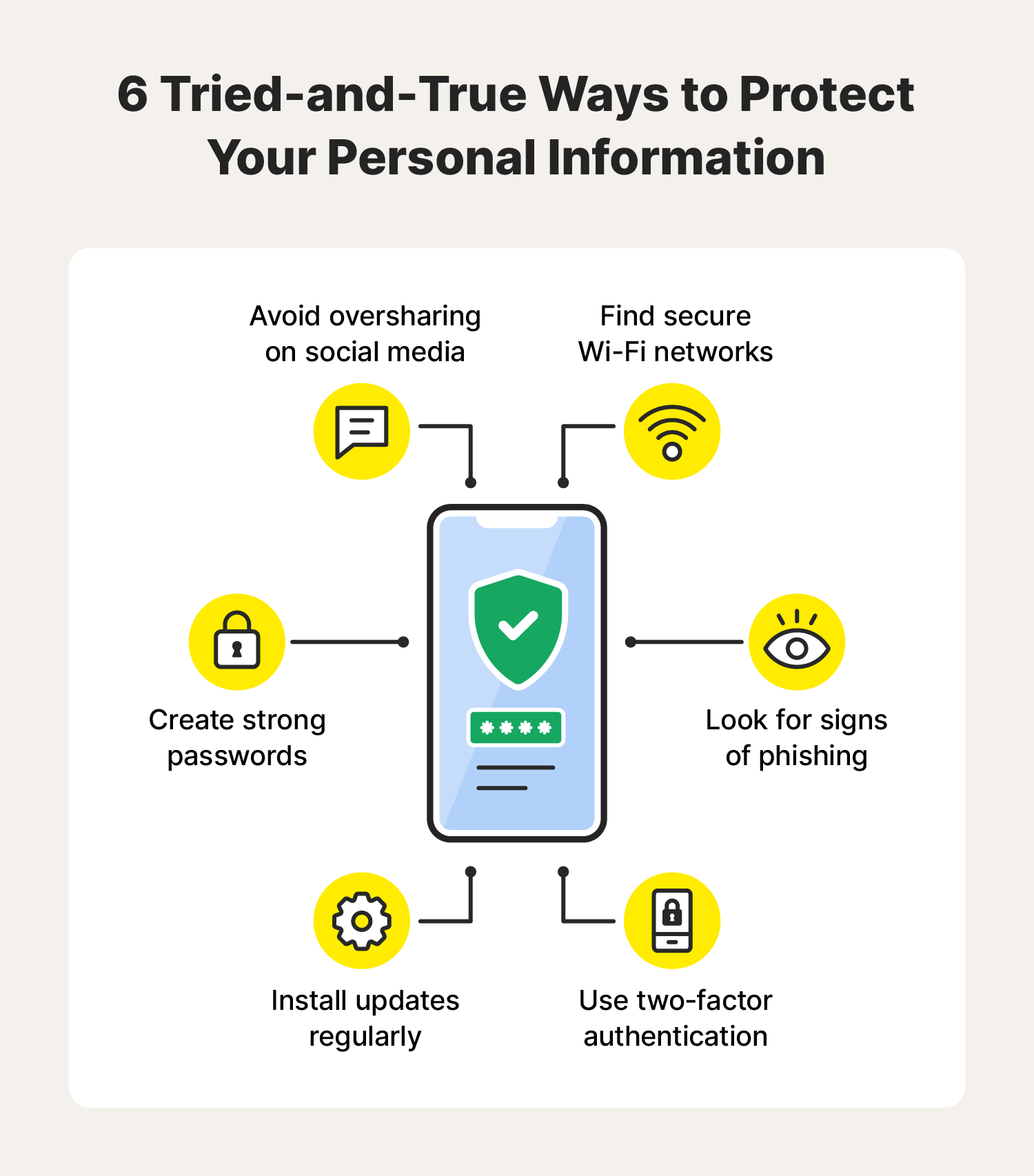
In today’s digital age, protecting personal data is more crucial than ever. Hackers are constantly on the prowl, looking for ways to steal sensitive information. But don’t fret! There are straightforward steps you can take to safeguard your data. Let’s dive into some practical tips that can help you stay one step ahead of cybercriminals.
Strong Passwords
Passwords are your first line of defense. Think of them as the lock on your front door. A strong password can keep unwanted visitors out. Here are some tips:
- Use a mix of letters, numbers, and symbols.
- Avoid using easily guessable words like “password” or “123456”.
- Change your passwords regularly.
It might be a bit of a hassle to remember complex passwords, but it’s worth it. Consider using a password manager to keep track of them.
Two-factor Authentication
Ever heard the saying “better safe than sorry”? Two-factor authentication (2FA) is an extra layer of security. It means you need more than just a password to access your accounts. Here’s how it works:
- You log in with your password.
- You receive a code on your phone or email.
- You enter the code to complete the login.
This way, even if someone gets hold of your password, they still can’t access your account without the second factor. It’s like having a deadbolt along with your regular lock.
Regular Software Updates
Software updates might seem annoying, but they are vital. They often include security patches that protect against new threats. Here’s a quick tip:
- Enable automatic updates on your devices.
Think of updates as vaccinations for your devices. They keep out the latest bugs and viruses.
Use Of Vpns
A Virtual Private Network (VPN) is like a secret tunnel for your internet traffic. It hides your online activities from prying eyes. Here’s why you should use a VPN:
- It encrypts your data, making it unreadable to hackers.
- It hides your IP address, protecting your identity.
- It allows you to browse safely on public Wi-Fi.
Imagine browsing the web in a café without a VPN. It’s like shouting your private information across the room. With a VPN, you’re whispering in a secure, private conversation.
By following these simple steps, you can significantly reduce the risk of your personal data being stolen. Stay safe and keep your information secure!
Recognizing Phishing Attempts
Phishing is one of the most common methods hackers use to steal personal data. It’s like a wolf in sheep’s clothing; it appears trustworthy but hides a dangerous intent. Recognizing phishing attempts can be the key to safeguarding your sensitive information. Let’s break down some tell-tale signs that you may be the target of a phishing scam.
Suspicious Links
One of the biggest giveaways of a phishing attempt is a suspicious link. If you receive an email or message with a link that looks odd, think twice before clicking. For example, you might receive an email from what appears to be your bank, asking you to click a link to verify your account. But if you hover over the link, you might notice that the URL looks fishy. Always double-check URLs and when in doubt, type the website address directly into your browser.
Unusual Requests
Hackers often make unusual requests that seem out of the blue. Imagine getting an email from a colleague asking for sensitive information or urgent money transfers. If this seems out of character, it probably is. Always verify such requests through a different communication channel before taking any action.
Generic Greetings
Phishing emails often use generic greetings like “Dear Customer” or “Hello User”. Legitimate companies usually address you by your name. If an email starts with a vague greeting, be cautious. This is often a sign that the email is a mass phishing attempt rather than a personalized message.
Spelling Errors
While everyone makes typos, phishing emails tend to have more than their fair share of spelling and grammatical errors. Hackers often don’t take the time to proofread their messages. So, if you notice multiple mistakes, it’s a red flag. For example, an email claiming to be from “Yur Bank” instead of “Your Bank” should immediately raise your suspicion.
By keeping these tips in mind, you can stay one step ahead of hackers and protect your personal data. Remember, vigilance is your best defense against phishing attempts.
Credit: lifelock.norton.com
Responding To Data Breaches
When personal data gets stolen, quick and effective actions can mitigate the damage. Responding to data breaches involves a series of steps to protect yourself and your information. Here’s what you need to know:
Immediate Actions
First, change your passwords. Use unique and strong combinations for each account. Avoid using the same password across multiple sites. Next, contact your bank or credit card company. Inform them about the breach. They may issue a new card or monitor your account for suspicious activity.
Notification Procedures
Notify affected parties quickly. This could be family, friends, or colleagues. They need to know their information might be compromised. Inform your workplace, too. They can take steps to protect their systems and data. If the breach involves your employer, follow their guidelines on reporting and response.
Monitoring For Fraud
Keep an eye on your credit reports. Look for any unusual activity. Report any suspicious transactions immediately. Many credit bureaus offer free monitoring services. Sign up to receive alerts for new accounts or changes to your report.
Long-term Security Measures
Consider using identity theft protection services. These services monitor for signs of identity theft. They can help resolve issues if your identity is stolen. Regularly update all your software. This includes antivirus programs, operating systems, and apps. Updates often fix security vulnerabilities. Finally, educate yourself about phishing scams and other common threats. Awareness is a key defense against future breaches.
Frequently Asked Questions
How Do Hackers Access Personal Information?
Hackers access personal information through phishing, malware, weak passwords, and exploiting software vulnerabilities. Always use strong passwords and update software.
What Techniques Do Hackers Use To Steal Your Personal Information?
Hackers use techniques like phishing, malware, keylogging, and social engineering to steal personal information. They exploit weak passwords and unsecured networks.
How To Prevent Your Data From Being Stolen?
Protect your data by using strong passwords, enabling two-factor authentication, updating software regularly, avoiding public Wi-Fi, and backing up data frequently.
How Can I Know If Someone Is Stealing My Data?
Monitor unusual account activity, check for unfamiliar devices, and watch for unexpected data usage. Use security software.
Conclusion
Protecting personal data is crucial today. Hackers constantly find new ways to steal it. Stay safe by using strong passwords. Update software regularly. Avoid suspicious emails and links. Use two-factor authentication whenever possible. Educate yourself and others about cyber threats.
Practice these habits to keep your data secure. Stay vigilant and proactive. Your safety online depends on it.

